Analyze with AI
Get AI-powered insights from this Mad Devs article:
Cyberattacks are on the rise, impacting businesses of all sizes. But what if you could predict and prevent these threats?
A cybersecurity risk assessment is your shield against the unknown. This process identifies potential vulnerabilities in your systems, data, and information assets. With this knowledge, you can create a targeted defense plan, prioritizing the areas most at risk.
In this article, you will discover the main points of conducting cybersecurity risk assessments and the various techniques and tools used to make the assessment qualitative and profitable. Check this article for valuable insights and guidance to help you avoid cyber threats.
Why perform a cybersecurity risk assessment?
Cybercrime is on the rise, and its impact is expanding as technology advances. A recent study by Cybersecurity Ventures predicts that cybercrime will cost the world over $10.5 trillion annually by 2025. It's not just the frequency of attacks that's increasing, but also the scope, affecting businesses of all sizes and industries:
- Ransomware rampage: According to a Sophos report, ransomware attacks surged by 78% in 2023, with an average ransom demand exceeding $200,000 per attack.
- Supply chain slaughterhouse: The number of supply chain attacks skyrocketed by 38% in 2023, according to SecurityScorecard, highlighting the interconnected nature of cyber risk.
- Phishing frenzy: Proofpoint research indicates phishing attacks remain a top threat, with a staggering 83% of organizations experiencing a successful phishing attack in 2023.
The good news: companies are starting to fight back. Despite a market dip in 2022, cybersecurity spending is on the rise. Gartner predicts global spending to reach a hefty $170.4 billion this year, highlighting a shift towards proactive defense.
But the cost of inaction is far greater:
IBM's 2024 Cost of a Data Breach Report reveals the average global cost of a data breach to be a record-breaking $4.35 million, with the healthcare industry experiencing the highest average cost at $10.1 million per breach.
Accenture's Cyber Threat Report 2024 estimates that cybercrime will cost businesses an average of $1.2 million per minute in 2024, showcasing the devastating impact of successful attacks.
So a large percentage of businesses have taken note and have increased their investment in cybersecurity measures.
Highlighting the importance of risk assessment in cybersecurity, we can point out the following problems that may arise if a risk assessment is not carried out.
- Data breaches. If proper security measures are not in place, sensitive information could be compromised. This could lead to a loss of reputation, financial losses, and legal consequences.
- Cyber attacks. Hackers can take advantage of vulnerabilities in your systems to steal data or cause disruption to your operations. This could result in a loss of productivity, damage to your reputation, and potential fines.
- Compliance violations. Failing to adhere to regulations such as GDPR or HIPAA could result in hefty fines, legal action, and damage to your reputation.
- System failures. If critical systems are not regularly tested and updated, they may become vulnerable to failures that can lead to costly downtime.
- Malware infections. Malicious software can infect your systems, compromising data and putting your organization at risk.
- Insufficient backups. If proper backup procedures are not in place, your organization may be unable to recover from a disaster. This could result in significant financial losses and damage to your reputation.
Investing in a cybersecurity risk assessment is an investment in your business's future. Don't wait for a breach to be your wake-up call. Take proactive steps to secure your digital assets and ensure business continuity in this ever-hostile digital landscape.
Overview of Cybersecurity Risk Assessment
A сybersecurity risk assessment is a systematic examination of an organization's security posture, evaluating its potential vulnerabilities and identifying the risks it faces from internal and external threats. It is critical to any company's cybersecurity strategy, allowing them to prioritize resources, allocate budgets effectively, and make informed decisions.
The specific type of assessment required for compliance will depend on the type of information being protected and the size and complexity of the organization. And its cost can range from a few thousand dollars for simple self-assessments to hundreds of thousands for comprehensive third-party audits.
📖 We explored the types of cybersecurity assessments in the article Types of Cybersecurity Assessments: Differences, Benefits, and Limitations.
Various industries and products have been regulated by specific standards that set the bar for their security measures. These standards are in place to protect sensitive information, whether it be personal data, health information, financial data, or even educational records. Some of the most prominent standards are provided in our related article, Cybersecurity Risk Assessment: Market Share and Industry Standards.
Risk assessment in cybersecurity primarily determines the system's current state, its potential vulnerabilities, and its consequences, while risk management continuously works to reduce risks and their consequences. And this is where you have to start from the beginning, paying enough attention to risk assessment; risk management works with its results.
Ready to build a robust cyber defense? Let's break down the steps involved in conducting a thorough cybersecurity risk assessment. This will provide you with a valuable template to get started.
How to perform a cybersecurity risk assessment
Before diving into risk assessment and mitigation, a solid understanding of your data, infrastructure, and their value is crucial. Here's how to establish this foundation:
1️⃣ Data audit:
- What data do we hold?
- Where and how is it stored?
- How is it protected and documented?
- Data retention: How long do we keep it?
- Data access: Who can access it internally and externally?
2️⃣ Define the assessment scope:
- What are we trying to achieve?
- What systems and data will be assessed?
- Are there budget or regulatory limitations?
- Who within the organization needs to be involved?
- Does the organization have a preferred risk analysis model?
Answering these questions helps ensure a focused and effective risk assessment. The next steps will delve deeper into each of these areas to build a comprehensive security plan.
Step 1. Identify the value
This first step focuses on classifying your assets based on their criticality to your business. It's like building a security wall around your most valuable resources. Why? Because limited resources are best directed toward protecting the most important data.
Establish a clear standard for determining asset importance. Consider factors like legal implications, potential financial penalties, and overall business value. Integrate this standard formally into your information security policy.
Once the standard is set, classify each asset as critical, major, or minor based on its importance.
Questions to consider in this step include:
- Are there legal penalties or financial losses associated with data exposure or loss?
- How valuable is this information to a competitor?
- Could this data be recreated? If so, what's the cost and time involved?
- Would losing this data impact revenue, profitability, or daily business operations?
- How would a data leak affect your company's reputation?
Step 2. Prioritize your assets
The second step involves creating a comprehensive inventory of your valuable assets. This detailed picture allows you to prioritize which assets need the most robust security measures.
Collaborate with business users and management to create a comprehensive list of all valuable assets. This can include buildings, employees, electronic data, trade secrets, vehicles and, of course, office equipment.
Remember: Not all assets hold the same value. Prioritize based on criticality.
For each identified asset, gather as much information as possible:
- Software used
- Hardware infrastructure
- Data types stored
- System interfaces
- End users accessing the asset
- Support personnel required
- Purpose and function of the asset
- Criticality to business operations
- Functional requirements
- Existing IT security policies
- IT security architecture
- Network topology details
- Information storage protection measures
- Information flow processes
- Technical security controls implemented
- Physical security controls in place
- Environmental security considerations
Then leverage a risk matrix to simplify asset prioritization. This tool visually represents the likelihood and impact of potential risks associated with each asset:
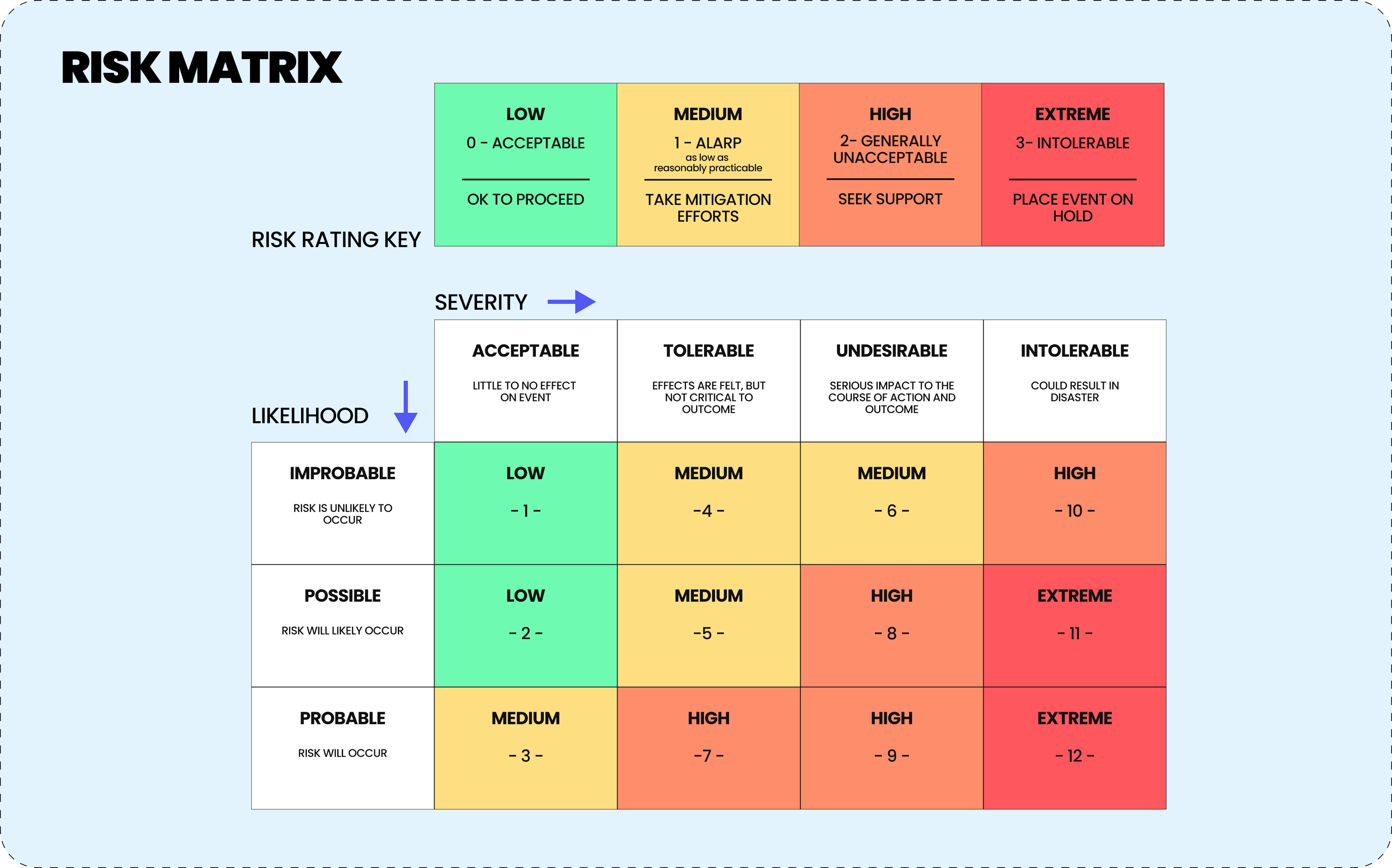
This allows you to focus your security efforts on the assets most susceptible to critical breaches. Additionally, a risk matrix can help evaluate risk exposure from third-party vendors.
Step 3. Identify potential threats
The next step is to identify the potential threats that could impact the assets. This should be based on a review of current and historical threat information and an analysis of the potential for new or emerging threats.
Step 4. Identify vulnerabilities
We've identified your valuable assets; now let's explore their vulnerabilities. A vulnerability is any weakness that could be exploited by a threat actor to gain access, steal data, or disrupt operations. Here's how to find them:
- Vulnerability scanning — Automated tools can scan your systems for known weaknesses based on industry databases like the National Institute of Standards and Technology (NIST). Additionally, vendor data, security audits, and incident response reports can reveal potential vulnerabilities.
➡️ Check our related Enhancing the GuardRails solution case study, where Mad Devs helped improve this security platform offering automated vulnerability scanning. - Patching & maintenance — Regular updates and proper patch management are crucial for addressing software vulnerabilities. Automatic updates ensure timely protection against known exploits.
- Physical security measures — Physical security is equally important. Keycard access control systems significantly reduce the risk of unauthorized access to hardware and servers.
- Attack surface management — This powerful strategy uses tools to monitor your entire digital footprint, identifying potential attack vectors. By minimizing these access points, you significantly reduce the risk of data breaches.
Step 5. Examining & strengthening controls
Now that you've identified vulnerabilities, let's explore your existing security controls and identify areas for improvement. Controls are measures taken to minimize the risk associated with a vulnerability.
Types of controls:
- Preventative controls aim to stop attacks before they occur. Examples include firewalls, encryption, antivirus software, and continuous security monitoring.
- Detective controls help detect if an attack has already happened. Examples include intrusion detection systems and continuous data leak detection.
Evaluate the effectiveness of your current controls in mitigating identified vulnerabilities. Are they:
- Do they address the specific threat or vulnerability?
- Do they provide a good value for the resources invested?
- Can they be realistically implemented and maintained?
Based on your analysis, identify and implement additional controls to address remaining vulnerabilities. Here are some examples:
- Technical: Two-factor authentication, automatic updates, and data loss prevention (DLP) tools.
- Non-technical: Security awareness training for employees, data security policies, and restricted physical access.
Step 6. Assess probability and impact
Now that we've identified your valuable assets, vulnerabilities, and existing controls, it's time to quantify the potential risks. This step involves analyzing the likelihood of a cyberattack and its potential impact on your organization.
Instead of a fearful "if" scenario, let's move towards a proactive "when" approach. By analyzing potential impact, we can develop strategies to mitigate the damage and ensure a smoother recovery process.
Many organizations use risk matrices that combine likelihood and impact into a single score. This score helps prioritize threats based on their overall risk level.
Step 7. Reporting and continuous improvement
The final step involves creating a comprehensive risk assessment report. This report serves as a critical resource for management in making informed decisions regarding budgets, security policies, and procedures. It should include:
✅ Detailed risk descriptions
Clear explanations of each identified threat and its associated vulnerabilities.
✅ Vulnerability and asset value assessment
Highlight the value of the assets at risk and the severity of potential vulnerabilities.
✅ Likelihood and impact analysis
Quantified assessments of the probability of each threat occurring and the potential impact it would have.
✅ Control recommendations
Proposed security controls and mitigation strategies for identified vulnerabilities.
Summary
Cybersecurity risk assessments are evaluations that identify and analyze potential risks to an organization's information systems and data. They help organizations understand the likelihood and impact of cyber threats and provide recommendations for mitigation. These assessments include reviewing technical systems, processes, policies, and the human element, such as employee training and awareness.
Performing regular cybersecurity risk assessments is crucial for organizations of all sizes and industries. They help organizations identify and mitigate potential cyber threats, improve security posture, and stay ahead of the curve regarding emerging risks. By taking proactive measures to assess and reduce cyber risk, organizations can protect their sensitive information and reputation and ensure the continued success of their business.
You now have a comprehensive understanding of the cybersecurity risk assessment and helpful tips and tools for getting the best out of it. And, of course, you can always ask Mad Devs for a free consultation on improving your product, making it the most flexible and reliable.









